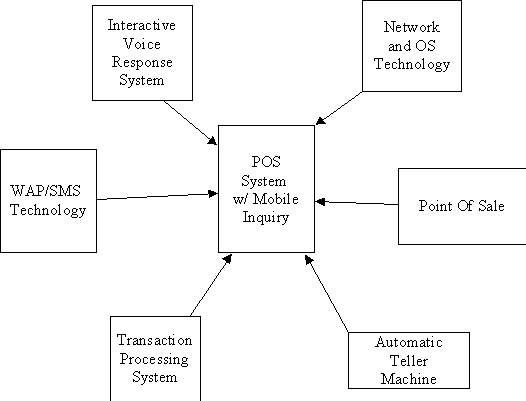
4.0 Theoretical Framework
The following figure illustrates the assembly of distinct theories that will be used in trying to make a POS System with Mobile Inquiry and IVRS.

The System that will be built will compose several technologies: Interactive Voice Response System, Network and OS Technology, Point-Of-Sale, Automatic Teller Machine, Transaction Processing System, and WAP/SMS Technology. These technologies and their components will be discussed in this chapter.
Interactive Voice Response System
An IVR System is a computerized system that allows a person, typically a telephone caller, to select an option from a voice menu and otherwise interface with a computer system. Generally the system plays pre-recorded voice prompts to which the person presses a number on a telephone keypad to select the option chosen, or speaks simple answers such as "yes", "no", or numbers in answer to the voice prompts [WIKJ2004].
IVR systems are found operating voicemail systems and telephone banking services, and are often the first point of contact when calling many larger businesses. These systems are generally used at the front end of call centers to identify what service the caller wants and to extract numeric information such as account numbers as well as provide answers to simple questions such as account balances or allow pre-recorded information to be heard [WIKJ2004].
IVR systems are often criticised as being unhelpful and difficult to use due to poor design and lack of appreciation of the callers' needs. A properly designed IVR system should connect callers to their desired service promptly and with a minimum of fuss [WIKJ2004].
The IVRS Technology that has been chosen for the system is a Perl Module IVRS for Linux implemented by Mukund Deshmukh <[email protected]>. It requires Perl 5.001 or later, a linux machine, and a compatible voice modem. According to Mukund it can play messages at a sampling rate of 11025 bytes/sec, get Caller ID (if the telephone line supports it), send and receive fax, record voice message, dial outside number, generate fast response, and interface with a database through Perl database interfaces. Programmers can do almost anything commercial IVRS are capable of.
The IVRS requires a standard voice modem (33.6kbps and above) which can understand AT voice commands. The writer has found that the Acer model AME-MA00 modem (AcerModem 56 Surf) works with the IVRS Perl Module. This will be used for building the system. It uses the serial port interface to the computer.
Network and OS Technology
The network components that will be needed by the system are: linux, LTSP, Etherboot, TFTP, NFS, DHCPD, X Windows system, Linux-HA, DRBD, STONITH, Heartbeat, OpenSSH, and VPN.
The Linux Operating System will be used in the POS terminals and the server cluster. Linux is one of the common Unix-type operating systems used in server clusters. Linux’ popularity is primarily driven by it being free [WIKD2004]. It is maintained mainly by Linus Torvalds with the help of a loosely knit group of programmers around the world. Linux being unix-like has the advantage of being very flexible and can be configured in a very wide variety of ways.
Linux can be configured to serve as a Terminal Server and a Thin Client. This setup simply means that all processes run in the main server and the clients machines basically only serve to be remote displays and input devices (keyboard, mouse, etc). In Linux the most common thin client setup is the Linux Terminal Server Project [MCQU2004] of Jim McQuillan and others. A LTSP setup simplifies software installation, maintenance, and upgrade across all workstations. Since the client will not do significant processing, the hardware requirements are but minimal therefore reducing cost per terminal.
LTSP, relies heavily on the network which is necessary booting the thin clients which includes the Etherboot ROM downloading the kernel using TFTP (Trifial File Transfer Protocol), the kernel mounting the root filesystem using NFS (Network File System), then obtaining an IP address via DHCP (Dynamic Host Configuration Protocol), then connecting the X Windows display server to the login screen in the server, and sending keystrokes and mouse movements to the server, and transmitting all display details back to the X server in the client machine. Each of these technology will be discussed in more detail below.
Etherboot is a package that enables diskless workstations to boot over the network by downloading the operating system from a TFTP Server. Etherboot ROMs can be burned in network card ROM chips, in the BIOS itself, or in a diskette. The diskette way is very common since all terminals purchase have a disk drive.
The Trivial File Transfer Protocol or TFTP is a very simple file transfer protocol akin to a basic version of ftp. It is often used to transfer small files between hosts on a network, such as when a remote X Windows System terminal or any other thin client boots from a network host or server. Some characteristics of TFTP are: 1) it uses UDP (port 69) as its transport protocol, 2) it cannot list directory contents, 3) there are not authentication or encryption algorithms, and 4) it can be used to write files to/from the remote server. [WIKL2004]
The Network File System or NFS is a protocol developed by Sun Microsystems which allows a computer to access files over a network as if they were on its local disks. NFS is stroly associated with UNIX systems though it can be used in any platform such as Macintosh and Microsoft Windows operating systems [WIKM2004].
The Dynamic Host Configuration Protocol provides a way to allocate IP addresses dynamically to computers on a local area network (LAN). A system administrator assigns a range of IP addresses to DHCP and each client computer on the LAN has its TCP/IP software configured to request an IP address automatically from the DHCP server when that client computer starts up. The request-and-grant process uses a lease concept with a controllable time period. This eases the network installation procedure on the client computer side considerably [WIKN2004].
In addition to the IP address, a DHCP server can provide other information like DNS server addresses, a DNS domain or a gateway IP address, for the convenience of the client computer[WIKN2004].
The X Window System (commonly X11 or X) is a windowing system for computers with bitmap displays. It is standard on Unix, Linux and other Unix-like operating systems and is available for most other modern operating systems. [WIKK2004].
X provides basic underpinnings for a graphical user interface (GUI): drawing and moving windows on a screen and interacting with a mouse and a keyboard. As per its maxim of "mechanism, not policy," X does not specify or provide the user interface itself — this is handled by user software. As such, the visual interface of X-based environments is highly variable; several different interface styles may coexist on one computer [WIKK2004].
X features network transparency: the machine where an application program runs (the application client) need not be the user's local machine (the display server). X's usage of the terms "client" and "server" is the reverse of what people often expect, in that the "server" is the user's local display rather than the remote machine[WIKK2004].
X originated at MIT in 1984. The current version, X11, was released in 1987. The project is now led by the X.Org Foundation. The current reference release is version 11 release 6.7.0 (X11R6.7.0)[WIKK2004] . X Windows is a requirement for setting up Linux Thin Clients with a Graphical Interface.
The Linux-HA project [ROBE2004] will be used for High-Availability of the main server cluster. Two identical servers are used in a primary/secondary setup. In the Linux-HA setup the secondary server will take over the IP address and all the services that run in the primary server. Data is synchronized between both servers using DRBD, a raid-mirror-over-the-network functionality available in Linux. A fully functional standby backup workstation will always be available to replace any failing terminal. Network cabling to all counter locations will also be redundant. Furthermore, all terminals, servers, and switches use UPSes to shield them from short power interruptions. Purchasing a generator is planned for immunity to longer power outages.
Reliability of a system is usually measured in maximum time per year wherein the system is down. A 90% guaranteed uptime means that in 365 days the system can only be offline 36.5 days. A 99% uptime guarantee equates to no more than 3.65 days downtime. A 99.99% uptime guarantee means no more than 8.7 hour downtime per year. Whether in hardware, networking, internet connections, or complete systems, the higher the reliability translates to higher cost [WIKH2004].
High-Availability is the property of a system as being highly reliable. A system is called Highly-Available when there is hardware redundancy and automatic takeover in case of server failure. Takeover time must be in insignificant seconds only.
Heartbeat is the main component of the Linux-HA project which takes care of monitoring the other server shutting down the other server using STONITH, starting and stopping services, and mounting the DRBD network device.
STONITH (Shoot The Other Node In The Head) hardware and software will be used to ensure that in case the primary server becomes partly disfunctional, the secondary server can turn the power off the primary server to ensure that the primary doesn’t interfere with the services of the secondary server.
A Server Cluster is a set of servers doing either different specific tasks or running the same services. The benefits of server clustering is load balancing, scalability, and reliability. Load balancing can be done by dividing the processing load to all the available servers. Scalability makes it possible to add servers when processing demand goes high and the possibility of removing or reassigning servers to different tasks when demand drops. In the event one of the servers in a redundant cluster fails, backup or secondary servers can take over processing with minimal or no service interruption. More redundancy equates to more reliability.
Aside from being highly available, a system must be also secure. System Security is the idea of the system being in the state immune from all known vulnerabilities and exploits that could, if used against the system, render it less useful or utterly useless. The proposed system will be locked down to only the POS application in the terminals. The planned web interface for supervisors will use SSL and require passwords. For accountability and history reasons, no transactions will be deleted in any event. A “canceled” transaction will be marked Canceled and exempted from computations but not deleted from the database. In addition to these, all transactions will have an operator and timestamp tag [WIKI2004].
For network security a Virtual Private Network or Tunnel is necessary to secure communication between the application server and database server which both in the campus backbone [WIKE2004]. The OpenSSH package will be used for this purpose encrypted and compressed port redirection [OPEN2004].
LTSP, Linux and the rest of the tools to be used in the project-thesis are all OpenSource. These software are mostly under the GNU General Public License (GPL) which, in a nutshell, permits anybody to replicate, modify, sell, or give away the software as long as the source code is not hidden. Opensource software is essential to anyone who is needs cost-efficiency [WIKF2004].
Point-Of-Sale
A Point-Of-Sale system is the frontend of retail shop, a checkout counter, or a variable location where transactions happen [WIKA2004]. POSes usually are computers built specially for the purpose. The set of input and output devices they usually are connected to are: bar code reader, keyboard, LCD display, monitor, receipt printer, network, and cash drawer. While most POSes are client-server systems some can operate as standalone and more interestingly as thin-client systems.
On the ergonomics part of the thesis-project, the POS User Interface is what the counters/cashier sees and uses [WIKG2004]. It is important to design the user interface in ways that will require minimum keystrokes and mouse movement to accomplish common tasks. Another design principle is ease of use wherein the position of the operator relative to the most common keys and other devices are considered for optimal operation. The physical positions of the input devices and monitors will also be made so as to make it comfortable to the operator to work for long periods. All these ergonomics are believed to contribute to operator accuracy, comfort and morale.
Bar code scanners and laser guns are a usual peripheral of POS terminals. Bar Code is Bar Code is an automatic identification technology. It allows data to be collected accurately and rapidly.
A Bar Code symbol consists of a series of parallel, adjacent bars and spaces. Predetermined width patterns are used to code actual data into the symbol. To read information contained in a Bar Code symbol, a scanning device, such as a light pen (or wand), is moved across the symbol from one side to the other. As a scanning device is moved across the symbol, the Bar Code width pattern of bars and spaces is analized by the Bar Code decoder, and the original data is recovered [SKAN1999].
The most visible application of this technology is the supermarket industry, where it has been in use since the 1970s. Bar Code is now the de facto automatic identification technology, for virtually any application [SKAN1999].
An important part of a POS is the User Interface. According to Jakob Neilsen [NEIL1994] the ten usability heuristics or rules of thumb are:
Visibility of system status
Match between system and the real world
User control and freedom
Consistency and standards
Error prevention
Recognition rather than recall
Flexibility and efficiency of use
Aesthetic and minimalistic design
Help users recognize, diagnoze, and recover from errors
Help and documentation
Automatic Teller Machine
An ATM is a machine permitting a bank’s customers to do transactions without the need for human tellers [WIKO2004]. Another name for ATMs are Information Kiosks. The project will only implement inquiry transactions in its ATM(s).
Transaction Processing System
A TPS is a computer system that responds immediately to user requests. Each request is considered to be a transaction. A transaction processing system is the opposite of a batched system [WEBO1996]. It is an interactive program which is usually online.
The problems addressed by TPSes are 1) the need to handle many simultaneous users, 2) the need to allow many users to work on the same set of data, with immediate updating, 3) the need to handle errors in a safe and consistent manner [HEI2004].
Most TPSes store their data in a Relational Database Management System that resides in a main server. The RDBMS is a set of programs and procedures that make it easy to manage databases as tables or relations [WIKB2004]. Examples of RDBMSes are PostgreSQL, MySQL, Oracle, MS SQL Server, IBM’s DB2, and Sybase SQL Server. Most modern RDBMS use SQL, structured query language, which is a declarative programming language for use in quasi-relational databases [WIKC2004].
WAP/SMS Technology
Wireless Application Protocol, or WAP, is the de facto standard for porting Internet services to wireless devices, like mobile phones and personal digital assistants (PDAs). WAP has been specifically designed to cope with small screens, error rates, and bandwidth limitations of cellular networks. It also makes it possible to transmit web pages without wires to cellular phones whole memory and processing power are limited. The WAP protocol stack is designed to deliver HTTP contents to mobile devices, through translation to the Wireless Markup Language (WML) pages, that are interpreted at the handset microbrowser. A WAP gateway is responsible for such operation and before transmission on the air interface, the gateway encodes the WML translation into a compact binary representation, in order to reduce data size on the wireless network [BENE2001].
Short message service (SMS) is a service available on most digital mobile phones that permits the sending of short messages (also known as text messages, or more colloquially texts or even txts) between mobile phones and other handheld devices. SMS was originally designed as part of the GSM digital mobile phone standard, but is now available on a wide range of networks, including 3G networks [WIKP2004].
The message payload is 140 bytes: either 160 7-bit characters, 140 8-bit characters, or 70 2-byte characters in languages such as Chinese, Korean, or Japanese when encoded using 2-byte UTF-16 character encoding (see Unicode). This does not include routing data and other metadata, which is additional to the payload size [WIKP2004].
________________________________________________________________________
|
Linux-Based Thin-Client Point Of Sale Systems with Mobile Application and IVRS |
4- |